Xiaomi smartphones are unanimously agreed to be one of the best value purchases available in the market at any point in time. Packing some insane hardware at some very lucrative price points, especially at the lower end of the smartphone market, these phones make an offer that a lot of people just can’t refuse. Xiaomi has also been receptive to the needs of the developer community, with decisions such as allowing bootloader unlocking without sacrificing the manufacturer’s warranty — a combination that a lot of other popular OEMs discard, as well as vastly improving upon their kernel source releases. These reasons make them one of the most popular devices in our forums, and they have rightfully earned that spot of popularity.
However, recent reports from security researchers point towards a worrying privacy issue observed on Xiaomi’s web browsers. Forbes’ cybersecurity contributor and associate editor Thomas Brewster, along with cybersecurity researchers Gabriel Cirlig and Andrew Tierney recently concluded in a report that Xiaomi’s various web browsers were sending data to remote servers. They allege that the data being sent included a history of all websites visited, including the URLs, all search engine queries, and all the items viewed on Xiaomi’s news feed, along with device metadata. What’s even worrying about this data collection allegation is that this data is being collected even if you seemingly browse with “incognito mode” enabled.
This data collection seemingly occurs on the pre-installed stock browser on MIUI, as well as Mi Browser Pro and Mint Browser, both of which are available for download through the Google Play Store. Together, these browsers have over 15 million downloads on the Play Store, while the stock browser is preloaded on all Xiaomi devices. The devices tested include the Xiaomi Redmi Note 8, Xiaomi Mi A1, Xiaomi Mi 10, Xiaomi Redmi K20, and the Xiaomi Mi Mix 3. There wasn’t a distinction between Xiaomi’s Android One or MIUI devices, as the collection code was found in the default browser anyway. As such, this issue does not appear to be MIUI-centric but depends on whether you use any of these three browsers on your device, irrespective of the underlying OS. Other browsers, like Google Chrome and Apple Safari collect far less data, restricting themselves to usage and crash analytics.
Xiaomi responded by seemingly confirming that the browsing data it was collecting was fully compliant with local laws and regulations on user data privacy matters. The collected information was user-consented and anonymized. However, the company denied the claims in the research.
The research claims are untrue. Privacy and security is of top concern.
This video shows the collection of anonymous browsing data, which is one of the most common solutions adopted by internet companies to improve the overall browser product experience through analyzing non-personally identifiable information.
The researchers, however, found this claim of anonymity to be dubious. The data that Xiaomi was sending was admittedly “encrypted”, but it was encoded in base64, which can easily be decoded. Since the browsing data can be decoded in a rather trivial manner, and since the collected data also contained device metadata, this browsing data could seemingly be correlated to the actions by individual users without significant effort.
Further, the researchers found that the Xiaomi browsers were pinging domains related to Sensors Analytics, a Chinese startup also known as Sensors Data, known for providing behavioral analytics services. The browsers also contained an API called SensorDataAPI. Xiaomi is also listed as a customer on the Sensors Data website.
Xiaomi has responded to the report from Forbes with denial on several aspects:
While Sensors Analytics provides a data analysis solution for Xiaomi, the collected anonymous data are stored on Xiaomi’s own servers and will not be shared with Sensors Analytics, or any other third-party companies.
The researchers responded against Xiaomi’s denial with further proof of their data collection practice.
The parameter data_list is the one I am interested in.
URL decode.
base64 decode.
Gunzip.
JSON data.
I don’t think that should be there. pic.twitter.com/5CYH5FU9E4
— Cybergibbons (@cybergibbons) April 30, 2020
With the information available at hand, there does appear to be a worrying privacy issue in the way these browsers function. We’ve reached out to Xiaomi for further comment on these claims.
Source: Forbes
Update 1: Xiaomi Responds in Blog Post
In an official blog post on Mi.com, Xiaomi strongly denied the allegations that they were violating user privacy.
“Xiaomi was disappointed to read the recent article from Forbes. We feel they have misunderstood what we communicated regarding our data privacy principles and policy. Our user’s privacy and internet security is of top priority at Xiaomi; we are confident that we strictly follow and are fully compliant with local laws and regulations. We have reached out to Forbes to offer clarity on this unfortunate misinterpretation.”
The company confirms that they collect “aggregated usage statistics data,” which includes “system information, preferences, user interface feature usage, responsiveness, performance, memory usage, and crash reports.” They state that this information “cannot alone be used to identify any individual.” They confirm that URLs are collected, but that this is done to “identify web pages which load slowly” so they can figure out “how to best improve overall browsing performance.”
Next, the company states that individual browsing data history is synced, but that this is only done when “the user is signed on Mi Account…and the data sync function is set to ‘On’ under Settings.” They deny that browsing data, apart from the aforementioned aggregated usage statistics data, is being synced when the user has enabled incognito mode.
Xiaomi then published screenshots of code snippets from one of their browser apps (they did not specify which browser, though) that they claim demonstrate their points. The first code snippet, according to Xiaomi, shows a decompiled method for “how [they] create randomly generated unique tokens to append to aggregate usage statistics.” They state that “these tokens do not correspond to any individuals.” The next code snippet is seemingly from the browser’s source code and shows a method for “how the Mi Browser works under incognito mode, where no user browsing data will be synced.” The third code snippet demonstrates that the aggregated usage statistics that Xiaomi collects are “stored on Xiaomi’s domain” and aren’t passed to Sensor Analytics. Finally, the fourth image “shows that usage statistic data is transferred with HTTPS protocol of TLS 1.2 encryption.”




To cap it all off, Xiaomi then cites 4 certifications their software has received from TrustArc and British Standard Institution (BSI). These certifications include ISO27001:2013, ISO27018:2014, ISO29151:2017, and TRUSTe.
In response to this blog post, cybersecurity researcher Andrew Tierney took to Twitter to refute Xiaomi’s claims. He states that he and several others re-confirmed the findings across multiple devices—that there “is no doubt that the Mint Browser sends search terms and URLS whilst in Incognito mode.” He states that the code that Xiaomi published does not demonstrate that their “randomly generated unique tokens” can’t be correlated to individuals. The researchers note that the UUID seems to persist across browsing sessions and only changes when the browser is re-installed. Whether Xiaomi only stores the data on their own servers or elsewhere was not a point of contention for the researcher, too. In addition, the researcher states that Xiaomi wasn’t accused of sending the data to remote servers through insecure methods—Mr. Tierney notes that the issue at hand is the data itself that is being sent.
We’re glad to see Xiaomi address these allegations directly, but the explanation does not seem to satisfy the researchers at this point. We will keep an eye on this story for further developments.
Update 2: Xiaomi to offer opt-out option in next browser update
Xiaomi has updated its blog post to announce that the next update to Mint Browser and Mi Browser will include an option in incognito mode to switch off the “aggregated” data collection. The software updates will be submitted to Google Play Store for approval today itself and should be available to users pretty soon.
It remains to be seen whether this data collection will remain enabled by default within the incognito mode, or not. We hope it isn’t. Still, having an option to opt-out works to address some privacy concerns.
Update 3: Xiaomi is updating its Mi Browser and Mint Browser to clarify its incognito data collection toggle
While Xiaomi did address the privacy concerns with a new settings toggle, what actually happened was that the language used for the toggle was misleading, achieving the opposite of what was written. As Android Authority points out, the “enhanced incognito mode” toggle said: “Aggregated data stats won’t be uploaded when incognito mode is on”, which led users to believe that flipping the toggle on would make this statement true. But this was not the case. The wording reflected the current state of the toggle, and was not a true/false statement that you change by flipping the switch.
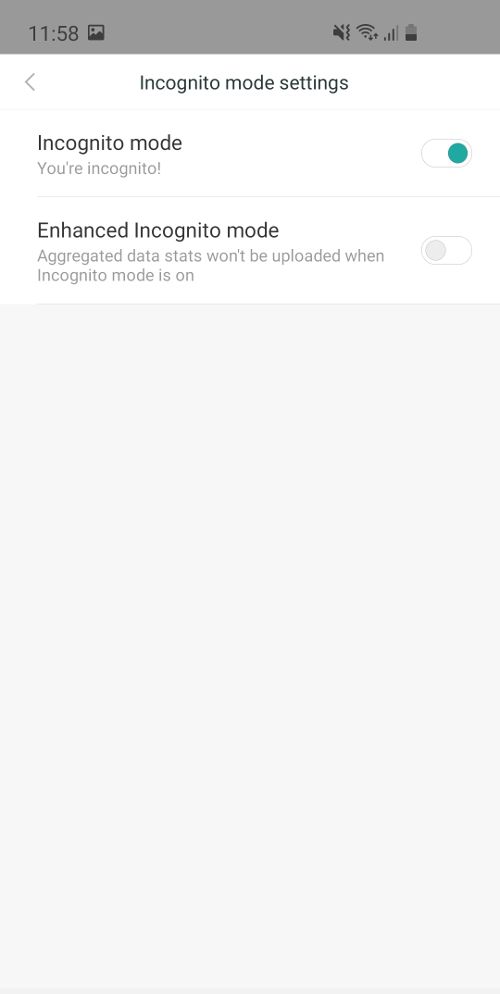
Old behavior
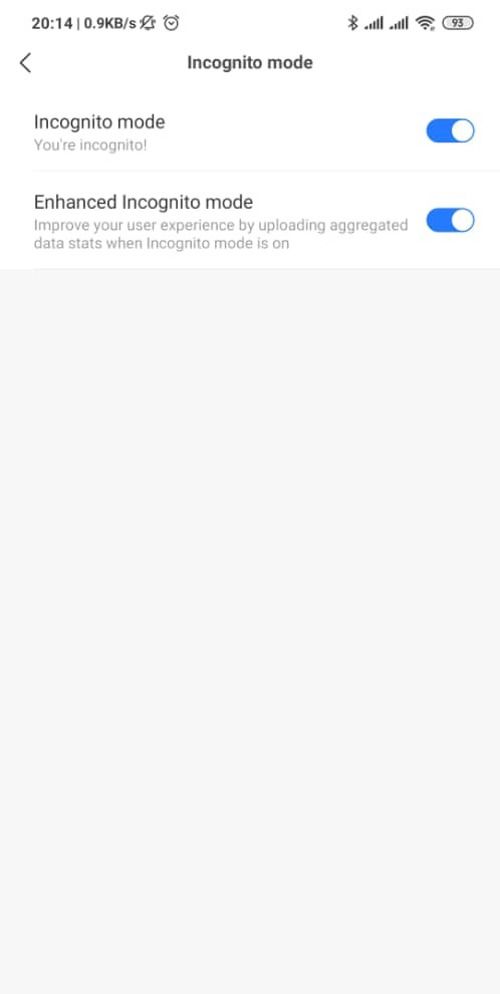
Now, Xiaomi has updated Mi Browser and Mint Browser to have better language on this toggle. The toggle is now called “Help us improve Mi/Mint Browser“, and the accompanying text says “Turn on to share usage stats with us when incognito mode is on“, with the text remaining the same when you flip the switch. This is much more clear to the purpose and the active state of the setting.


New behavior
In both the versions, the toggle needs to be in the off state if you wish to not have your data collected in incognito mode. It’s just the text that is changing to better reflect the state. The new update to both the browsers is being pushed to the Google Play Store.
The post [Update 3: Clearer Toggle Language] Researchers accuse Xiaomi web browsers of collecting browsing data – even in Incognito mode appeared first on xda-developers.
from xda-developers https://ift.tt/2KQ8aZD
via IFTTT

Aucun commentaire:
Enregistrer un commentaire